Dynamic Information Flow Tracking
From NUEESS
Jcmartinez (Talk | contribs) (→Abstract) |
Jcmartinez (Talk | contribs) (→The General Idea) |
||
| (6 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
== Abstract == | == Abstract == | ||
| - | Dynamic information flow tracking (DIFT) | + | Dynamic information flow tracking (DIFT) is an effective security countermeasure for both low-level memory corruptions and high-level semantic attacks. However, many software approaches suffer large performance degradation, and hardware approaches have high logic and storage overhead. In this paper, we propose a flexible and light-weight hardware/software co-design approach to perform DIFT based on secure page allocation. Instead of associating every data with a taint tag, we aggregate data according to their taints, i.e., putting data with different attributes in separate memory pages. Our approach is a compiler-aided process with architecture support. The implementation and analysis show that the memory overhead is little, and our approach can protect critical information, including return address, indirect jump address, and system call IDs, from being overwritten by malicious users. |
| - | |||
| - | + | == The General Idea == | |
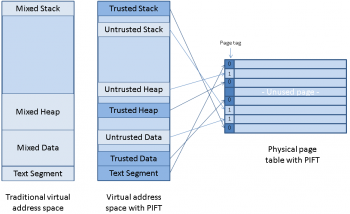
| + | [[File:pift-idea.png |thumb|right|350px|Virtual adreess space and page table on PIFT]] | ||
| + | |||
| + | == The Architectural Design == | ||
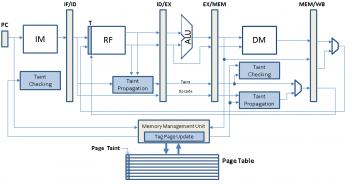
| + | [[File:pift-architecture.png |thumb|right|350px|Architecture design]] | ||
| + | |||
| + | == People == | ||
| + | |||
| + | * [[ Juan Carlos Martinez Santos]] | ||
| + | |||
| + | == Publications == | ||
| + | |||
| + | *J. C. Martinez Santos, Y. Fei, and Z. J. Shi, “PIFT: Efficient dynamic information flow tracking using secure page allocation,” in WkShp on Embedded System Security (WESS) (held in conjunction with Embedded Systems Week), Oct. 2009. | ||
Latest revision as of 13:51, 28 March 2012
Contents |
Abstract
Dynamic information flow tracking (DIFT) is an effective security countermeasure for both low-level memory corruptions and high-level semantic attacks. However, many software approaches suffer large performance degradation, and hardware approaches have high logic and storage overhead. In this paper, we propose a flexible and light-weight hardware/software co-design approach to perform DIFT based on secure page allocation. Instead of associating every data with a taint tag, we aggregate data according to their taints, i.e., putting data with different attributes in separate memory pages. Our approach is a compiler-aided process with architecture support. The implementation and analysis show that the memory overhead is little, and our approach can protect critical information, including return address, indirect jump address, and system call IDs, from being overwritten by malicious users.
The General Idea
The Architectural Design
People
Publications
- J. C. Martinez Santos, Y. Fei, and Z. J. Shi, “PIFT: Efficient dynamic information flow tracking using secure page allocation,” in WkShp on Embedded System Security (WESS) (held in conjunction with Embedded Systems Week), Oct. 2009.
| Whos here now: Members 0 Guests 0 Bots & Crawlers 1 |